Highest standards - in encryption, control, and certification.

ISO 27001
We are certified according to the ISO27001:2022 standard.

ISO 27001
We are certified according to the ISO27001:2022 standard.

ISO 27001
We are certified according to the ISO27001:2022 standard.

ISO 27001
We are certified according to the ISO27001:2022 standard.

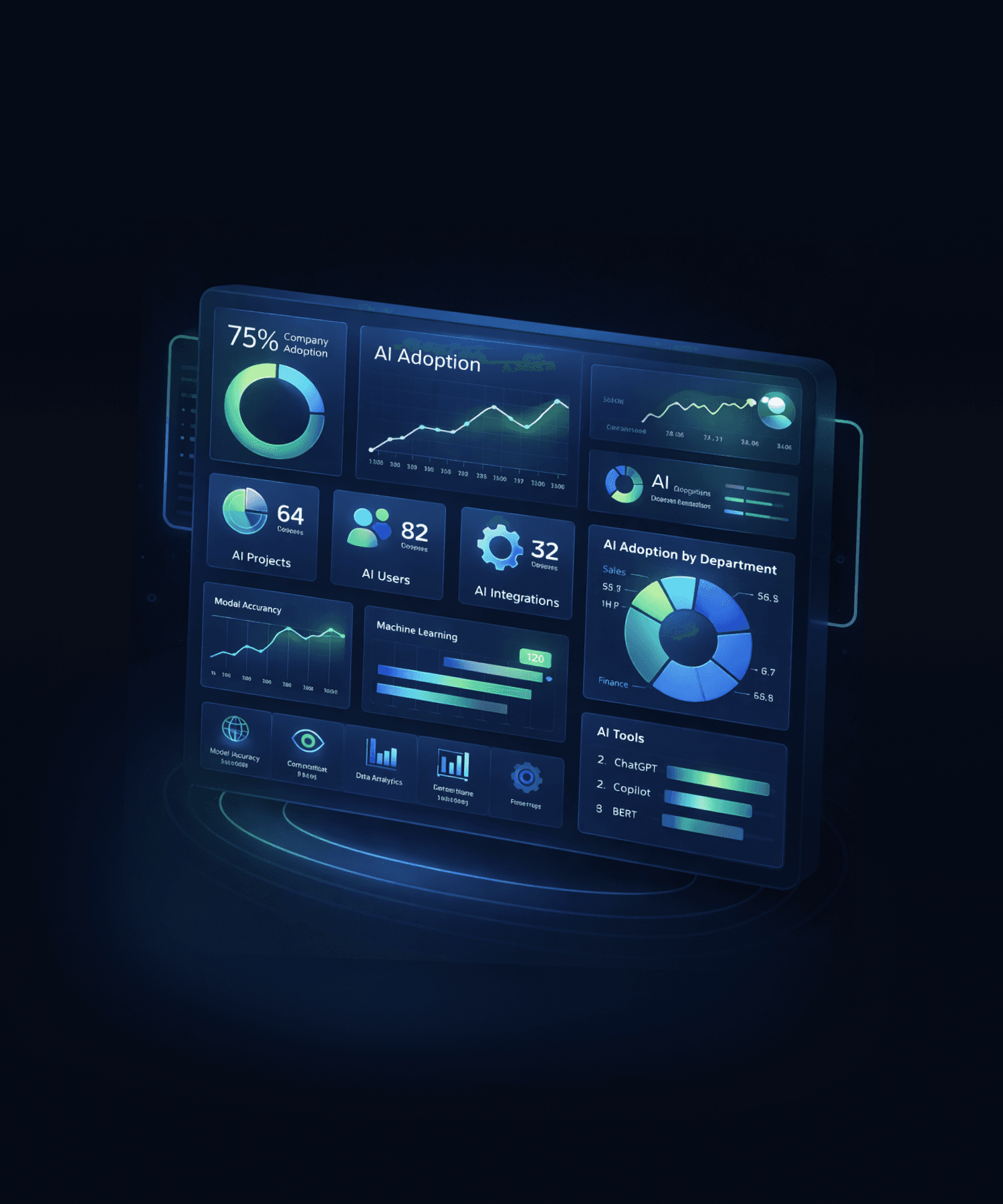
Enterprise Ready Security
SSO, RBAC system, Entra ID, and audit logs.

Enterprise Ready Security
SSO, RBAC system, Entra ID, and audit logs.

Enterprise Ready Security
SSO, RBAC system, Entra ID, and audit logs.

Enterprise Ready Security
SSO, RBAC system, Entra ID, and audit logs.

No training data
We separate your data almost completely from that of other customers.

No training data
We separate your data almost completely from that of other customers.

No training data
We separate your data almost completely from that of other customers.

No training data
We separate your data almost completely from that of other customers.

Per tenant encryption
Encryption of data at rest (AES256) and in transit (TLS 1.3).

Per tenant encryption
Encryption of data at rest (AES256) and in transit (TLS 1.3).

Per tenant encryption
Encryption of data at rest (AES256) and in transit (TLS 1.3).

Per tenant encryption
Encryption of data at rest (AES256) and in transit (TLS 1.3).

GDPR-compliant
Full compliance with EU data protection regulations

GDPR-compliant
Full compliance with EU data protection regulations

GDPR-compliant
Full compliance with EU data protection regulations

GDPR-compliant
Full compliance with EU data protection regulations
German Data Center
We host our own redundant infrastructure with dedicated servers in German data centers.

German Data Center
We host our own redundant infrastructure with dedicated servers in German data centers.

German Data Center
We host our own redundant infrastructure with dedicated servers in German data centers.

German Data Center
We host our own redundant infrastructure with dedicated servers in German data centers.




Your data belongs to you. Period.
Your data belongs to you. Period.
The most important difference from public AI models? We don't learn from you. meinGPT serves as a secure proxy layer between your company and the LLM providers.
The most important difference from public AI models? We don't learn from you. meinGPT serves as a secure proxy layer between your company and the LLM providers.
We guarantee contractually and technically that your inputs (prompts) and uploaded documents will never be used to train the AI models. What happens in your company stays in your company.
We guarantee contractually and technically that your inputs (prompts) and uploaded documents will never be used to train the AI models. What happens in your company stays in your company.
We implement these security measures in detail.

Dedicated infrastructure
We operate our platform on dedicated servers in highly available Kubernetes clusters with strictly separated environments for core platform, AI applications, and sandboxes. (Managed Kubernetes, encrypted Control Plane, separate clusters)

Isolated AI execution
All AI-generated content is processed in specially secured AI sandboxes that are isolated from each other through virtualization in addition to containerization. (Container and VM isolation, no direct access to platform data)

Secure supply chain
All container images are automatically checked for security vulnerabilities before use and regularly rescanned to minimize risks in the software supply chain. (Image Scanning, Runtime Checks, verified images)

Dedicated infrastructure
We operate our platform on dedicated servers in highly available Kubernetes clusters with strictly separated environments for core platform, AI applications, and sandboxes. (Managed Kubernetes, encrypted Control Plane, separate clusters)

Isolated AI execution
All AI-generated content is processed in specially secured AI sandboxes that are isolated from each other through virtualization in addition to containerization. (Container and VM isolation, no direct access to platform data)

Secure supply chain
All container images are automatically checked for security vulnerabilities before use and regularly rescanned to minimize risks in the software supply chain. (Image Scanning, Runtime Checks, verified images)

Dedicated infrastructure
We operate our platform on dedicated servers in highly available Kubernetes clusters with strictly separated environments for core platform, AI applications, and sandboxes. (Managed Kubernetes, encrypted Control Plane, separate clusters)

Isolated AI execution
All AI-generated content is processed in specially secured AI sandboxes that are isolated from each other through virtualization in addition to containerization. (Container and VM isolation, no direct access to platform data)

Secure supply chain
All container images are automatically checked for security vulnerabilities before use and regularly rescanned to minimize risks in the software supply chain. (Image Scanning, Runtime Checks, verified images)

Dedicated infrastructure
We operate our platform on dedicated servers in highly available Kubernetes clusters with strictly separated environments for core platform, AI applications, and sandboxes. (Managed Kubernetes, encrypted Control Plane, separate clusters)

Isolated AI execution
All AI-generated content is processed in specially secured AI sandboxes that are isolated from each other through virtualization in addition to containerization. (Container and VM isolation, no direct access to platform data)

Secure supply chain
All container images are automatically checked for security vulnerabilities before use and regularly rescanned to minimize risks in the software supply chain. (Image Scanning, Runtime Checks, verified images)

Client encryption
Customer data is stored encrypted and additionally secured per tenant, so an incident is always confined to a single tenant. (Combination of platform key and tenant key, documents, chats, knowledge bases)

Strict access control
Access to systems and data is role-based and secured through multi-factor authentication; productive infrastructure is reserved exclusively for a very small, defined group of individuals. (RBAC, MFA, restricted support roles)

Controlled AI data flows
Requests to AI models are technically anonymized, so model providers cannot draw conclusions about individual clients, while providing full transparency about the deployed providers. (EU-based providers, configurable model selection)

Client encryption
Customer data is stored encrypted and additionally secured per tenant, so an incident is always confined to a single tenant. (Combination of platform key and tenant key, documents, chats, knowledge bases)

Strict access control
Access to systems and data is role-based and secured through multi-factor authentication; productive infrastructure is reserved exclusively for a very small, defined group of individuals. (RBAC, MFA, restricted support roles)

Controlled AI data flows
Requests to AI models are technically anonymized, so model providers cannot draw conclusions about individual clients, while providing full transparency about the deployed providers. (EU-based providers, configurable model selection)

Client encryption
Customer data is stored encrypted and additionally secured per tenant, so an incident is always confined to a single tenant. (Combination of platform key and tenant key, documents, chats, knowledge bases)

Strict access control
Access to systems and data is role-based and secured through multi-factor authentication; productive infrastructure is reserved exclusively for a very small, defined group of individuals. (RBAC, MFA, restricted support roles)

Controlled AI data flows
Requests to AI models are technically anonymized, so model providers cannot draw conclusions about individual clients, while providing full transparency about the deployed providers. (EU-based providers, configurable model selection)

Client encryption
Customer data is stored encrypted and additionally secured per tenant, so an incident is always confined to a single tenant. (Combination of platform key and tenant key, documents, chats, knowledge bases)

Strict access control
Access to systems and data is role-based and secured through multi-factor authentication; productive infrastructure is reserved exclusively for a very small, defined group of individuals. (RBAC, MFA, restricted support roles)

Controlled AI data flows
Requests to AI models are technically anonymized, so model providers cannot draw conclusions about individual clients, while providing full transparency about the deployed providers. (EU-based providers, configurable model selection)
Monitoring & Anomaly Detection
Security-related activities are centrally logged and continuously monitored to detect anomalies early and respond effectively. (Audit logs, AI-based anomaly detection)

Tests & Assurance
The platform is regularly tested for vulnerabilities through external grey-box penetration tests and internal security audits. (Biannual pentests, continuous scans)

Compliance & Transparency
Our security organization is oriented towards established standards and is transparently documented for customers. (ISO-27001-based ISMS, Trust Center, EU data centers)

Monitoring & Anomaly Detection
Security-related activities are centrally logged and continuously monitored to detect anomalies early and respond effectively. (Audit logs, AI-based anomaly detection)

Tests & Assurance
The platform is regularly tested for vulnerabilities through external grey-box penetration tests and internal security audits. (Biannual pentests, continuous scans)

Compliance & Transparency
Our security organization is oriented towards established standards and is transparently documented for customers. (ISO-27001-based ISMS, Trust Center, EU data centers)

Monitoring & Anomaly Detection
Security-related activities are centrally logged and continuously monitored to detect anomalies early and respond effectively. (Audit logs, AI-based anomaly detection)

Tests & Assurance
The platform is regularly tested for vulnerabilities through external grey-box penetration tests and internal security audits. (Biannual pentests, continuous scans)

Compliance & Transparency
Our security organization is oriented towards established standards and is transparently documented for customers. (ISO-27001-based ISMS, Trust Center, EU data centers)

Monitoring & Anomaly Detection
Security-related activities are centrally logged and continuously monitored to detect anomalies early and respond effectively. (Audit logs, AI-based anomaly detection)

Tests & Assurance
The platform is regularly tested for vulnerabilities through external grey-box penetration tests and internal security audits. (Biannual pentests, continuous scans)

Compliance & Transparency
Our security organization is oriented towards established standards and is transparently documented for customers. (ISO-27001-based ISMS, Trust Center, EU data centers)
We are far from done.
We always strive for higher safety standards to meet the ever-increasing demands of our customers.




ISO 27001 Certification
ISO 27001 Certification
2025
2025
2026
SOC 2 Type II Audit






ISO 42001 AI Management System
ISO 42001 AI Management System
2026
2026
2026
SOC 2 Type II Audit



Frequently Asked Questions about Security
Does myGPT support Single Sign-On (SSO)?
add
How is the data encrypted?
add
Where is my data physically located?
add
Will my data be used for training OpenAI?
add
Does myGPT support Single Sign-On (SSO)?
add
How is the data encrypted?
add
Where is my data physically located?
add
Will my data be used for training OpenAI?
add
Does myGPT support Single Sign-On (SSO)?
add
How is the data encrypted?
add
Where is my data physically located?
add
Will my data be used for training OpenAI?
add
Does myGPT support Single Sign-On (SSO)?
add
How is the data encrypted?
add
Where is my data physically located?
add
Will my data be used for training OpenAI?
add

Start with AI!
Join over 500 companies of all sizes and implement AI in your business. With meinGPT, you can prevent uncontrolled use of AI in your company and cover most use cases on a user-friendly platform.


Start with AI!
Join over 500 companies of all sizes and implement AI in your business. With meinGPT, you can prevent uncontrolled use of AI in your company and cover most use cases on a user-friendly platform.


Start with AI!
Join over 500 companies of all sizes and implement AI in your business. With meinGPT, you can prevent uncontrolled use of AI in your company and cover most use cases on a user-friendly platform.


Start with AI!
Join over 500 companies of all sizes and implement AI in your business. With meinGPT, you can prevent uncontrolled use of AI in your company and cover most use cases on a user-friendly platform.

ISO 27001-konform
Sicherheitsarchitektur auf Enterprise-Niveau

Entwickelt in Deutschland.
Besuch uns in München. 🥨

Europäisches Hosting
Gehosted in Deutschland & der EU


About Company
Sicherheitsarchitektur auf Enterprise-Niveau

About Company
Besuch uns in München. 🥨

About Company
Gehosted in Deutschland & der EU


ISO 27001-konform
Sicherheitsarchitektur auf Enterprise-Niveau

Entwickelt in Deutschland
Besuch uns in München 🥨

Europäisches Hosting
Gehosted in Deutschland & der EU


ISO 27001-konform
Sicherheitsarchitektur auf Enterprise-Niveau

Entwickelt in Deutschland.
Besuch uns in München. 🥨

Europäisches Hosting
Gehosted in Deutschland & der EU